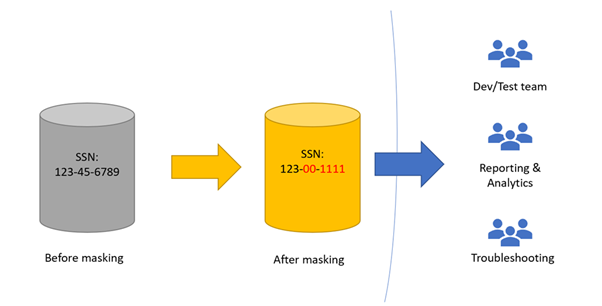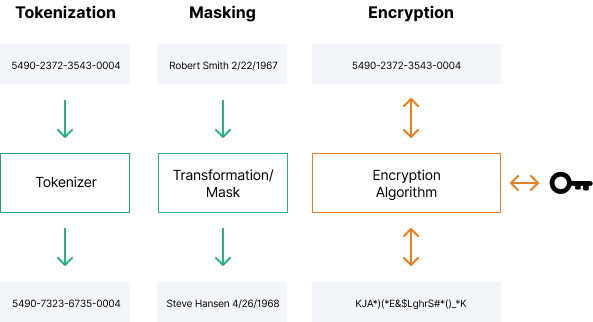
Data Obfuscation Vs Data Masking Ppt Powerpoint Presentation Infographics Outline Cpb | PowerPoint Templates Backgrounds | Template PPT Graphics | Presentation Themes Templates

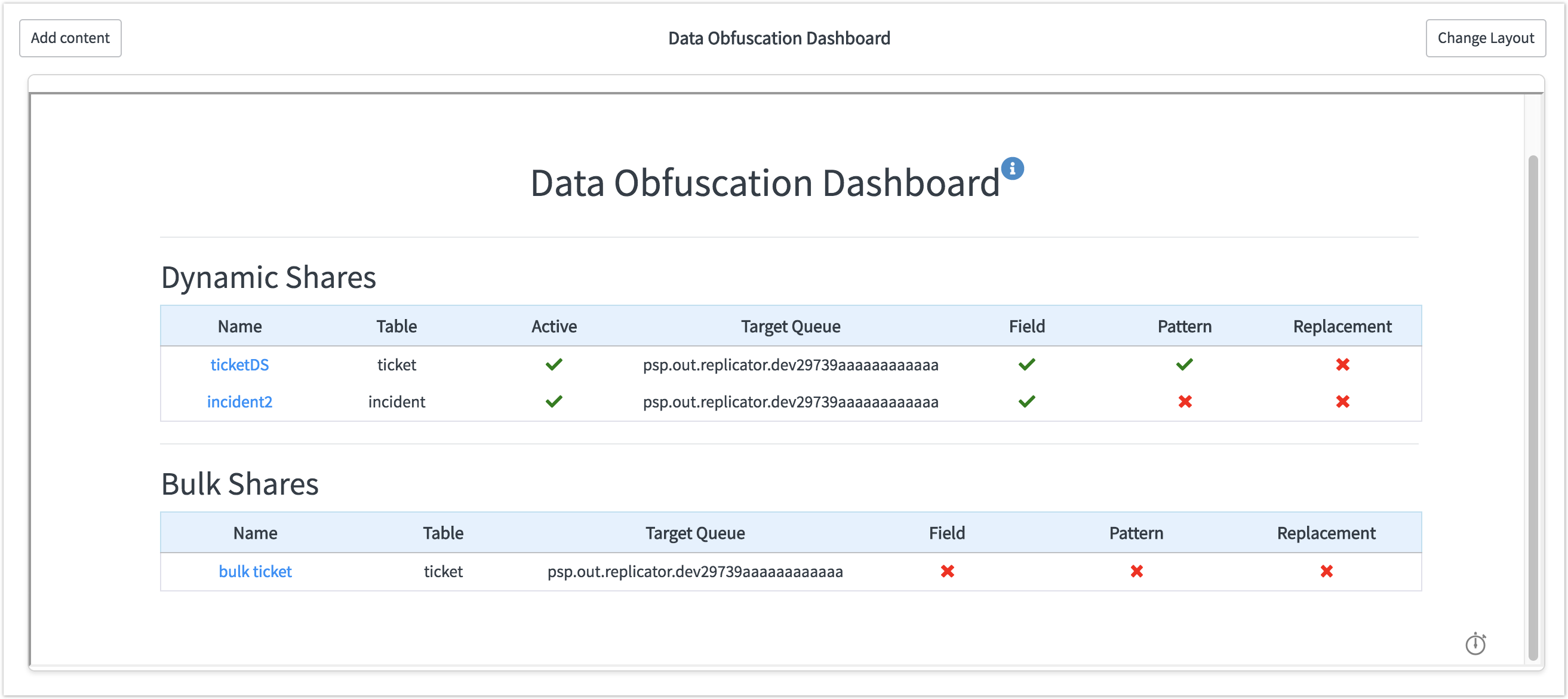
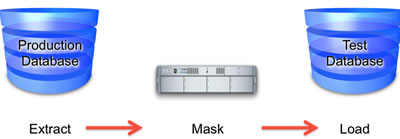
MySQL Security – MySQL Enterprise Data Masking and De-Identification | dasini.net - Diary of a MySQL experts